- Market-Inspector.co.uk
- Blog
- Cyber Security for SMEs
Is Your SME Ready in Case of a Cyber Attack?
Protect Your SME from Cyber Attacks
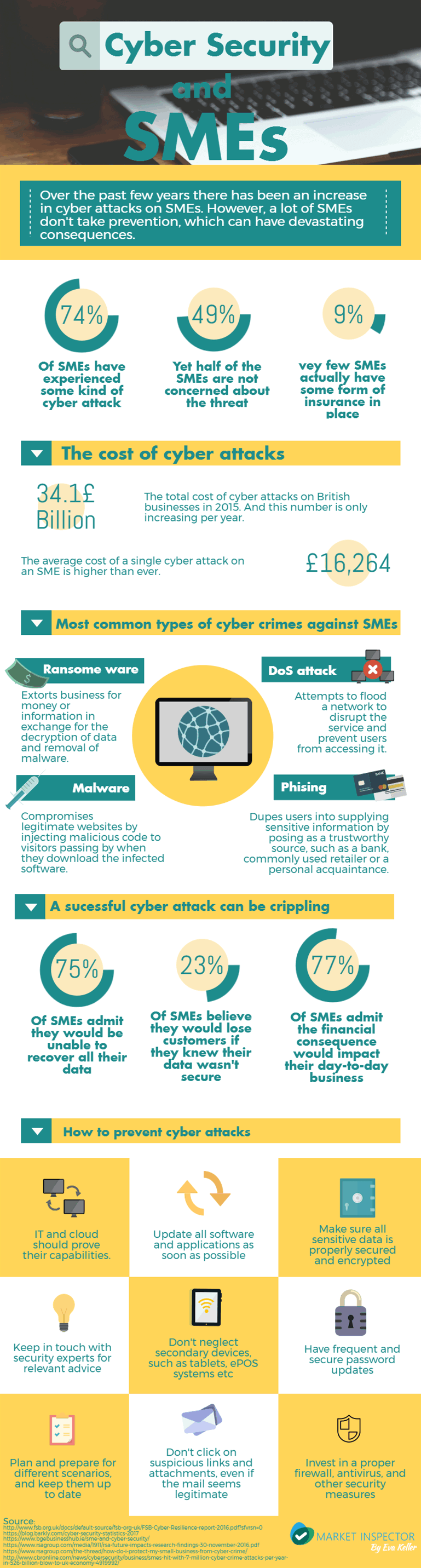
In a day and age where companies thrive thanks to technology, there are unfortunately a number of problems that arise at the same time. And a growing concern for business these days are security related, cyber security to be more specific. With the majority of data being stored in the cloud, and a record number of secondary online devices such as ePOS systems, there are plenty of vulnerabilities to exploit.
And these attacks are not uncommon. We have all heard about big cyber-attacks, gaps in security and leaks. Global corporations fall victim to it all the time. However, contrary to popular belief, the most common victims are small to medium business. Research shows that 3 out of 4 SMEs experienced some form of cyber-attack in 2015.
Why Are SMEs Being Targeted by Cyber Attacks?
Despite these statistics, most SMEs feel they are not at risk of being a target of a cyber-attack. Thinking their small size protects them, making them uninteresting targets for those coming cybercrime. However the reality is that their size works against them. SMEs are less likely to have strong security measures in places, and are much more likely to be susceptible to being hacked.
And an unprepared SME can suffer devastating consequences from an unexpected cyber-attack. In a lot off cases there is no plan of how to react in case such an attack happens, or how to deal with the consequences. This can result in a number of problems, from loss of data, customer, revenue etc. and that doesn’t even take to cost of putting a system back in place into account.
If you want to know more about the consequences of cyber-attacks on SMEs, or ways prevent them, take a look at the infographic bellow.
If you would like to use this infographic on your website, use the embed code below:
We strive to connect our customers with the right product and supplier. Would you like to be part of Market Inspector?

